DevSecOps friendly Kubernetes Security Solution
Protect your K8s environment, from securing the infrastructure to applications running in containers. Safeguard sensitive data, maintain system stability, and prevent unauthorized access with Kubernetes security built for runtime protection, threat detection, and regulatory compliance.
GET STARTED
Robust Kubernetes security solution tailored for enterprise deployment
Safeguard clusters, containers, and pods against potential threats
Kubernetes has become the de-facto standard for container orchestration, with over 78% organizations using it. However, securing Kubernetes environments remains a key challenge:
- Over 62% Kubernetes deployments are severely misconfigured/unsecured
- Top security risks include misconfigurations, vulnerable containers, and insider threats
AccuKnox brings an easy-to-use Kubernetes security solution specially built for runtime protection, threat detection, and compliance. Containers have a large attack surface and vulnerabilities in Kubernetes deployments can lead to serious data breaches, outages, and compliance issues.
Our Cloud-Native Application Protection Platform (CNAPP) is an enterprise-ready Kubernetes security solution to manage these risks. With capabilities like runtime guardrails, anomaly detection, and automated response, AccuKnox prevents threats, detects suspicious activities, and enables quick incident response.
Why AccuKnox for Kubernetes Security
Protects over
47873 +
Containers Scans/Day
Blocks over
39731 +
Escape Attempts/Month
750000 +
Open source downloads with immense community support and assistance
Key Kubernetes Security Challenges Faced by Organizations
- Network Security
- Identity & Access
- Securing Containers
- Monitoring & Detection
Network Security
The flat network topology and dynamical allocation of IP addresses makes network segmentation very complex. Any compromised pod can leverage this to laterally access other pods/nodes.
- Nodes, pods and services not isolated
- Cryptojacking malware could spread between pods to mine cryptocurrency.
- Lack of network segmentation and access controls
Are you convinced? Take the next Step
Prevent, detect, and respond to secure every second seamlessly in your cloud infrastructure.
Zero Trust Kubernetes Security Platform
AccuKnox enables a Zero Trust approach within Kubernetes environments with its patented solutions:
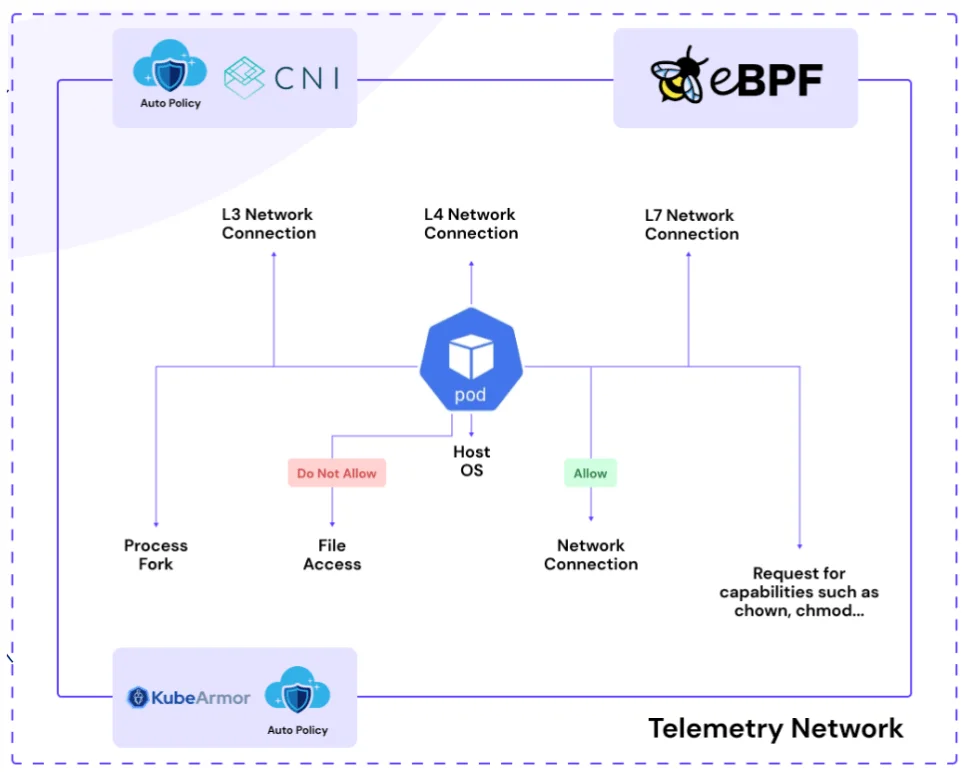
- Runtime Guardrails: System-level policies restrict container activities preventing attacks like breakouts, cryptojacking, hidden processes etc. Machine learning detects anomalies signaling threats.
- Incident Response: Automated responses like killing processes, quarantining pods etc. instantly contain threats minimizing blast radius. Detailed audit logs accelerate forensic investigations.
- Compliance Reporting: Pre-built templates map controls to standards like PCI, HIPAA etc. to simplify audits. Reports prove compliance to regulators.
AccuKnox secures Kubernetes deployments with:
- Restrict Containers: Set system-level policies to restrict container activities
- Enforce Security: Runtime enforcement of fine grained controls
- Detect Threats: Machine learning to detect anomalies and threats
- Respond Quickly: Auto-triggers responses to security incidents
- Simplify Complexity: Easy to define high-level guardrails
How Does This Help Your Organization?
- Prevent attacks before they happen
- Enforce Security: Runtime enforcement of fined-grained controls
- Detect threats early
- Respond instantly to incidents
- Prove compliance with reports
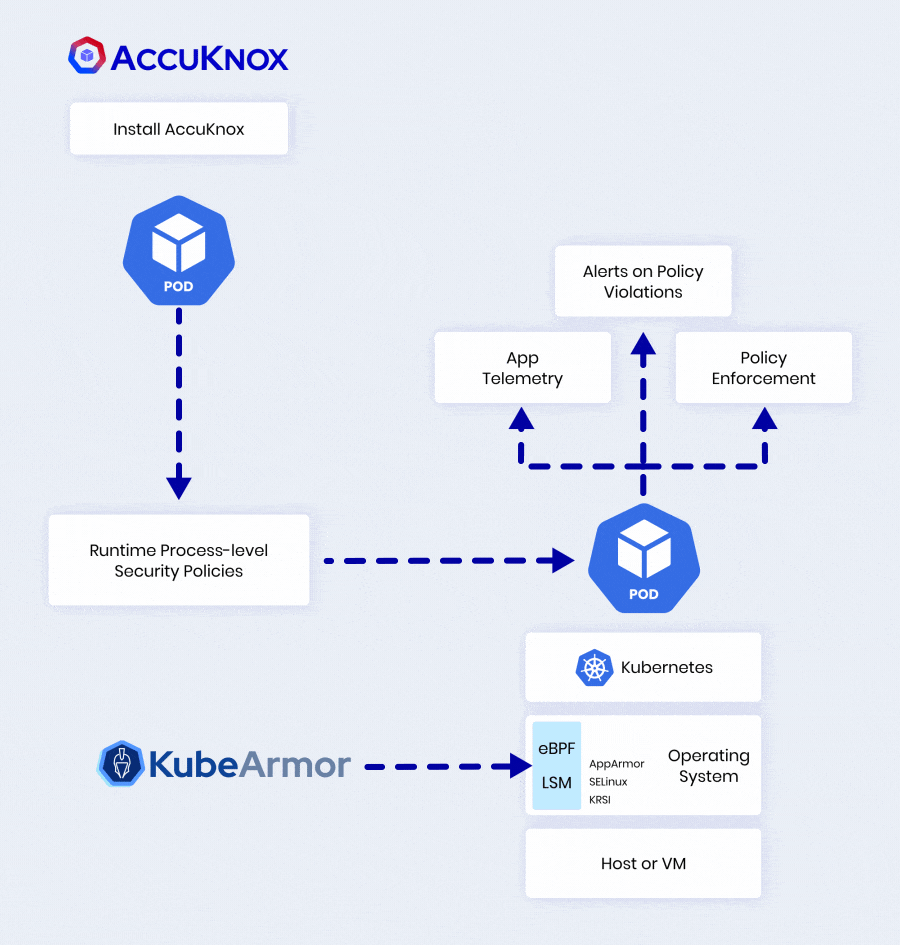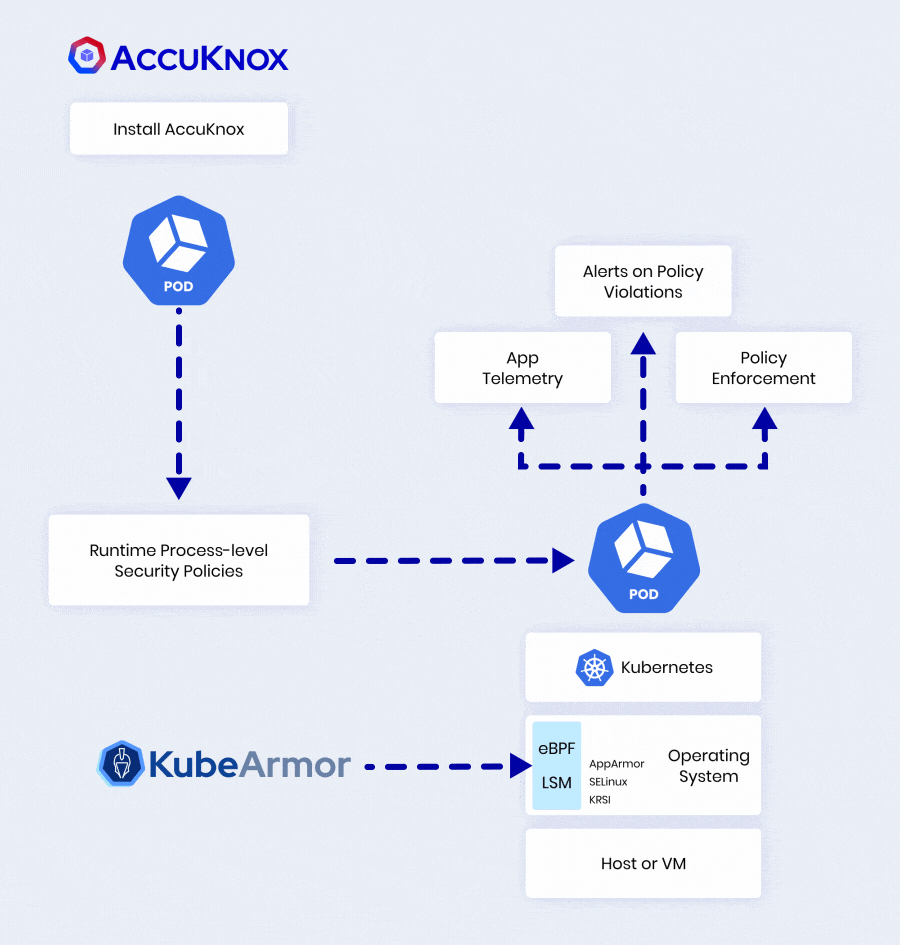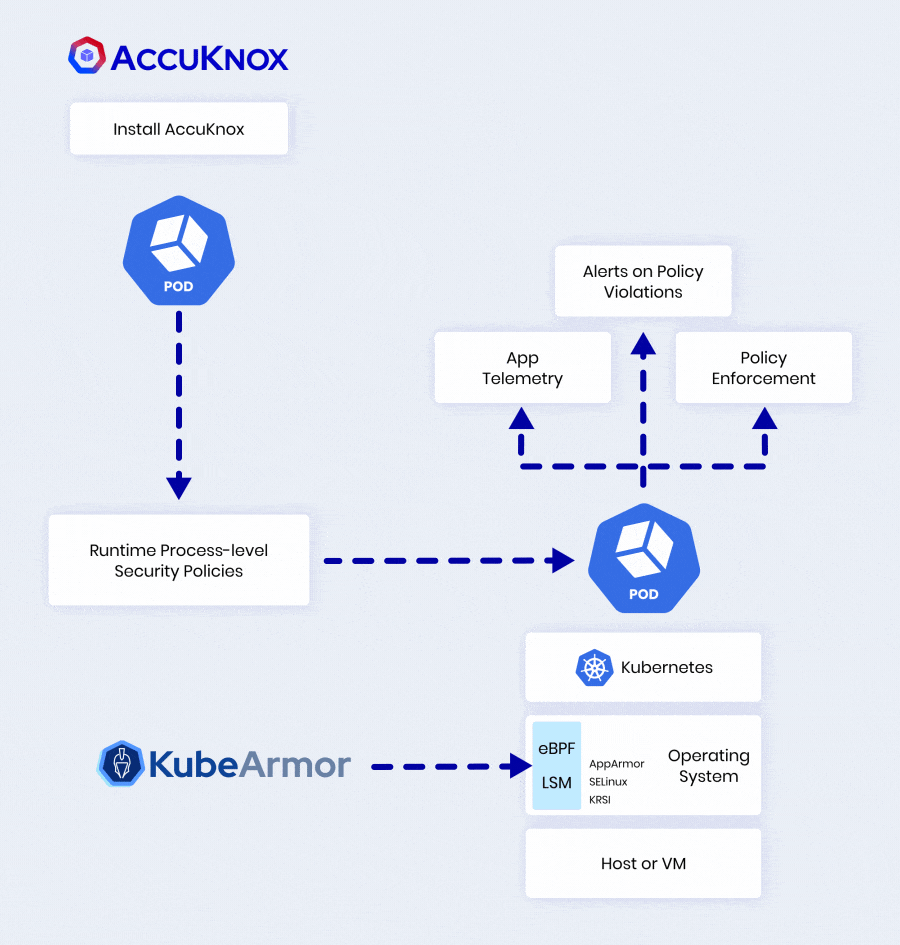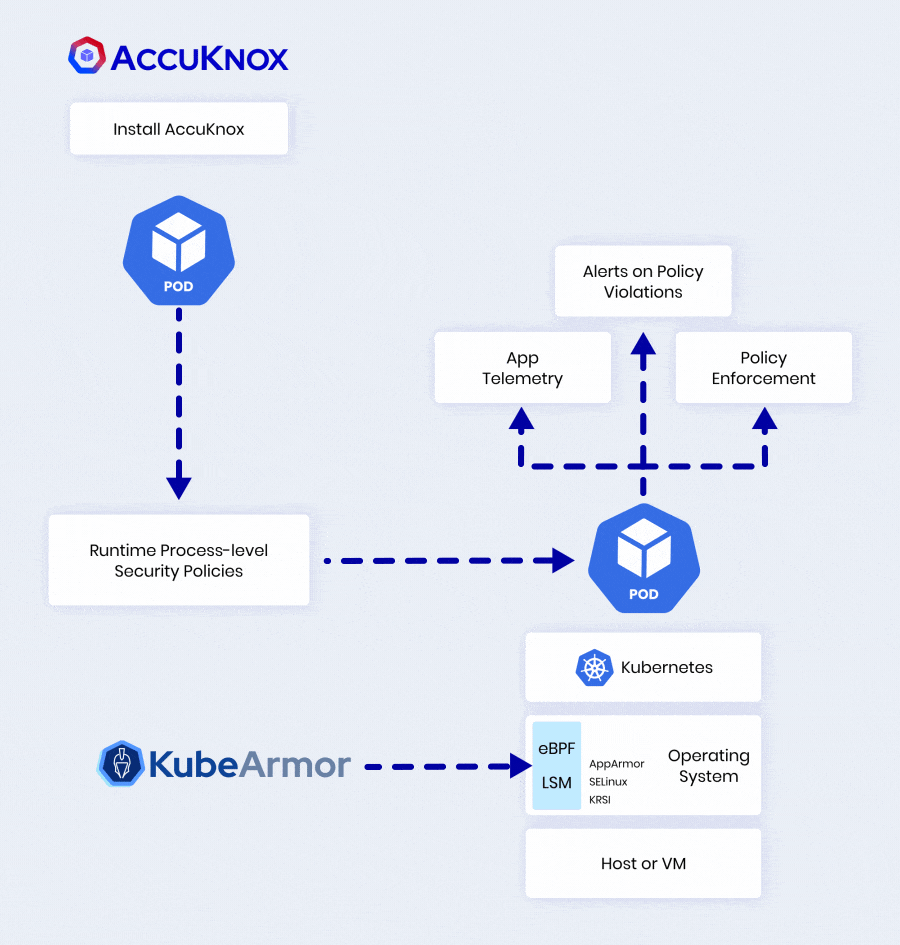
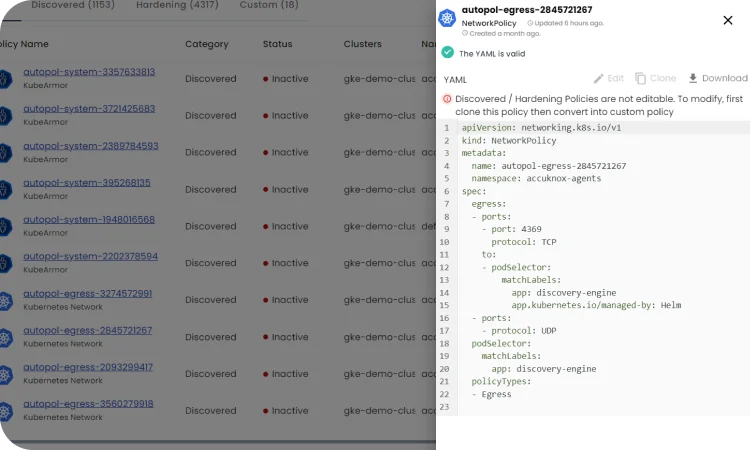
Key Capabilities of AccuKnox to Secure Kubernetes (K8s)
Runtime Guardrails
| Policy Type | Description |
|---|---|
| System Call Policies | Allow/block execute, chroot, pivot_root, ptrace etc. |
| I/O Control Policies | Allow/block read, write, mmap on files, dirs, sockets, pipes etc. |
| Network Control Policies | Allow/block connect, listen, accept on IP, port, protocol |
Threat Detection
- Detects malicious activities like privilege escalations, breakout attempts, crypto mining, hidden processes etc.
- Triggers auto-responses like alerts, killing processes, quarantining pods etc.
Compliance & Forensics
- Detailed audit logs for forensic investigations
- Maps logs to MITRE ATT&CK framework
- Simplifies compliance reporting
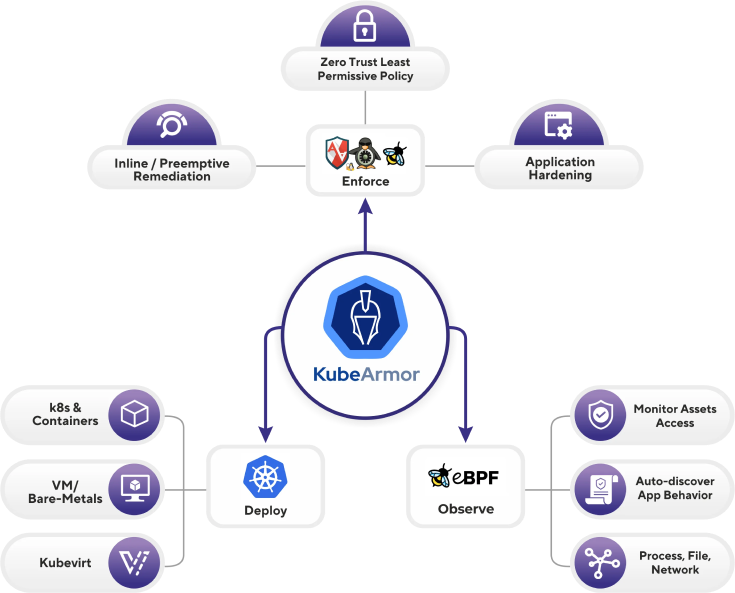
AccuKnox offers the easiest way to get enterprise-grade security for Kubernetes
- Purpose-built solution: For securing Kubernetes environments, using patented micro-segmentation technology and Linux primitives for comprehensive visibility and control over container activities.
- Simple DevSecOps Flow: AccuKnox CNAPP integrates with Kubernetes constructs for easy deployment and management, offering pre-built templates for security posture and intuitive dashboards for DevOps teams to manage policies and respond to threats.
- Proactive and Efficient: Lightning fast protection in production environments, requiring minimal changes to applications or infrastructure, and offering runtime protection across 50 microservices in under 1 hour.
- Compliance Checks: Simplified compliance with PCI-DSS, HIPAA, and CIS benchmarks by providing pre-built reports and detailed audit logs, reducing auditing effort, and ensuring compliance with external tools.
- Trusted by Industry Leaders: 24×7 security assurance with continuous runtime protection, adaptive behavioral models, maintenance upgrades, and enterprise support, ensuring peace of mind for evolving applications and infrastructure.
Trusted By Global Innovators

Common questions on Kubernetes Security, answered!
Kubernetes Security includes actions, processes and principles to ensure security in deployment. It deals with securing containers, configuring cloud-based workloads, network security and infrastructure hardening.
Kubernetes Security revolves around Authorization and Authentication for zero-trust access within the cluster.
The right Kubernetes Security setup safeguards critical applications which reside on the cloud and are open to complex exploit strategies. It is also mandatory to fulfil compliance requirements, fix API vulnerabilities and limit unrestricted network access.
Network security, identity and access management, securing containers, and monitoring/detection.
Misconfigurations, vulnerable container images, API vulnerabilities, and unrestricted network access. If not identified and fixed on time, it usually leads to a lot of gaps in the security system which can be breached/exploited down the line.
Role-Based Access Control (RBAC), network policies, TLS encryption, and authentication. Kubernetes expects you to configure and use TLS to provide data encryption in transit within the control plane, and between the control plane and its clients.
A security context configures a pod or container’s privilege and access control settings, including personalized access control based on user and group IDs. It is useful to secure connections and operations.
The 4C’s of cloud-native security are cloud, clusters, containers, and code. The Cloud Native security model’s layers build on one another.
Kubernetes has 2 types of security contexts: internal and external.
- Internal Security Contexts are defined within the pod or container.
- External security contexts are defined outside the pod or container.
The security context is related to, but not the same as, Kubernetes Role-Based Access Control (RBAC). RBAC is used for a wide range of Kubernetes resources, including pods, nodes, and entire clusters. The security context grants permissions exclusively to pods.
- Image scanning.
- Host operating system hardening.
- Base container images help reduce the attack surface.
- Harden your Kubernetes clusters.
- Integrating security tools into Kubernetes clusters.
Untrusted code usage, which gives threat actors access to it without your awareness and may contain hidden malware. Containerised apps usually contain unnecessary packages or libraries that can be hacked. Removing these superfluous packages to start securing.
Unsecured identity access management solutions lead to unnecessary privileges for users. Ingress controllers using open-source NGINX software in Kubernetes clusters are also vulnerable. Malicious xApps can redirect traffic, inject commands, and obtain secret credentials.
- Containers running with privileged flags.
- Using insecure images.
- Container and Kubernetes misconfiguration.
- Unprotected communication between containers.
- Vulnerabilities like container escape in CRI-O runtime.
- Enable secret encryption while they’re at rest.
- Turn on or set up least-privilege access to secrets for RBAC rules.
- Limit access to certain containers in secret.
- Consider 3rd Party Secret Store suppliers.